Safeguarding the Oil & Gas Sector from Growing Cyber Threats
The oil and gas industry is exposed to persistent and evolving cyber risks—from ransomware campaigns targeting critical infrastructure to exploitation of remote access systems and cloud vulnerabilities. Protecting high-value assets, executive personnel, and security control systems is more urgent than ever.
Critical cyber threats undermining the oil & gas industry
As digital systems become tightly integrated with physical operations, the energy sector faces a growing range of cyber threats that can disrupt critical infrastructure, expose sensitive data, and compromise profitability.
Protection of Operational Technology (OT) Systems
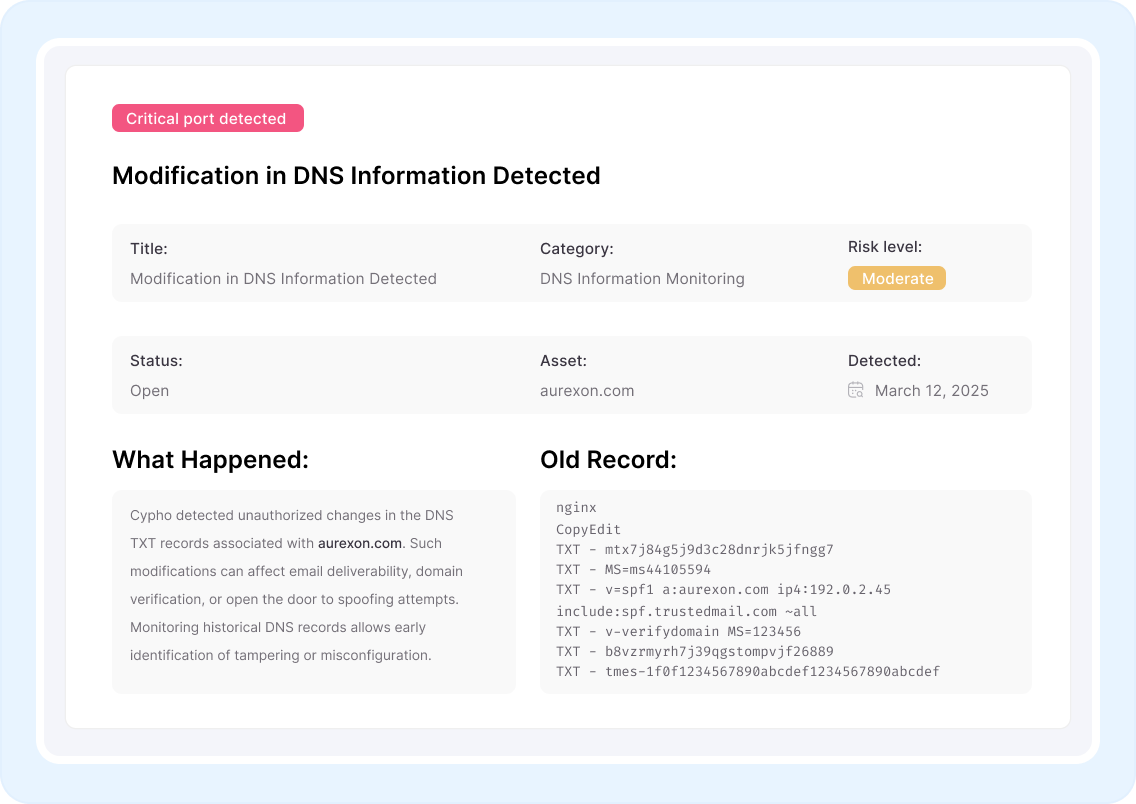
Oil and gas companies rely on industrial control systems (ICS), SCADA networks, and operational technology to manage extraction, refining, and distribution. These systems are increasingly connected to IT networks, exposing them to cyber threats that can disrupt production, compromise safety mechanisms, and cause environmental hazards. Cypho monitors for exposed OT assets, leaked configurations, and threat actor campaigns targeting energy infrastructure.
Ransomware Targeting Energy Infrastructure
Ransomware groups increasingly target oil and gas companies to disrupt pipeline operations, refinery processes, and supply chain logistics. These attacks can halt production, trigger safety incidents, and cause significant financial losses across the energy supply chain.
Supply Chain & Third-Party Risk Monitoring
Energy companies depend on complex supply chains involving drilling contractors, equipment vendors, and logistics partners. Compromised third-party credentials, exposed APIs, and vendor vulnerabilities create entry points for attackers targeting upstream and downstream operations.
Executive & VIP Impersonation Protection
Threat actors target C-suite executives and key personnel in the energy sector through spear-phishing, domain spoofing, and social engineering campaigns to gain access to sensitive operational data, financial systems, and strategic communications.
Legacy Industrial Systems & Vulnerability Exposure
Aging SCADA systems, legacy PLCs, and outdated firmware in oil and gas environments are difficult to patch and often lack modern security controls, creating persistent vulnerabilities across critical infrastructure.
Strategic cybersecurity solutions for oil & gas infrastructure
Empowering energy companies to proactively maintain uninterrupted operations.
Operational intelligence for sustainable business
Integrate cybersecurity insights into your operational decision-making to support long-term resilience. By correlating threat data with asset importance, geographic risk, and business impact, Cypho helps to maintain secure operations while optimizing productivity and safety.
Integrated brand across digital landscape
Continuous threat monitoring across systems