Stay Ahead of Emerging Threats with Context-Aware Vulnerability Intelligence
Cypho’s vulnerability intelligence connects the dots between misconfigurations, active threat actors, and asset-specific risks, helping you prioritize what truly matters. Empower your security teams with actionable insights, enriched threat context, and seamless integration into your existing workflows.
Get the full picture with intelligent vulnerability prioritization
Cypho helps you focus on the vulnerabilities that pose the greatest risk.
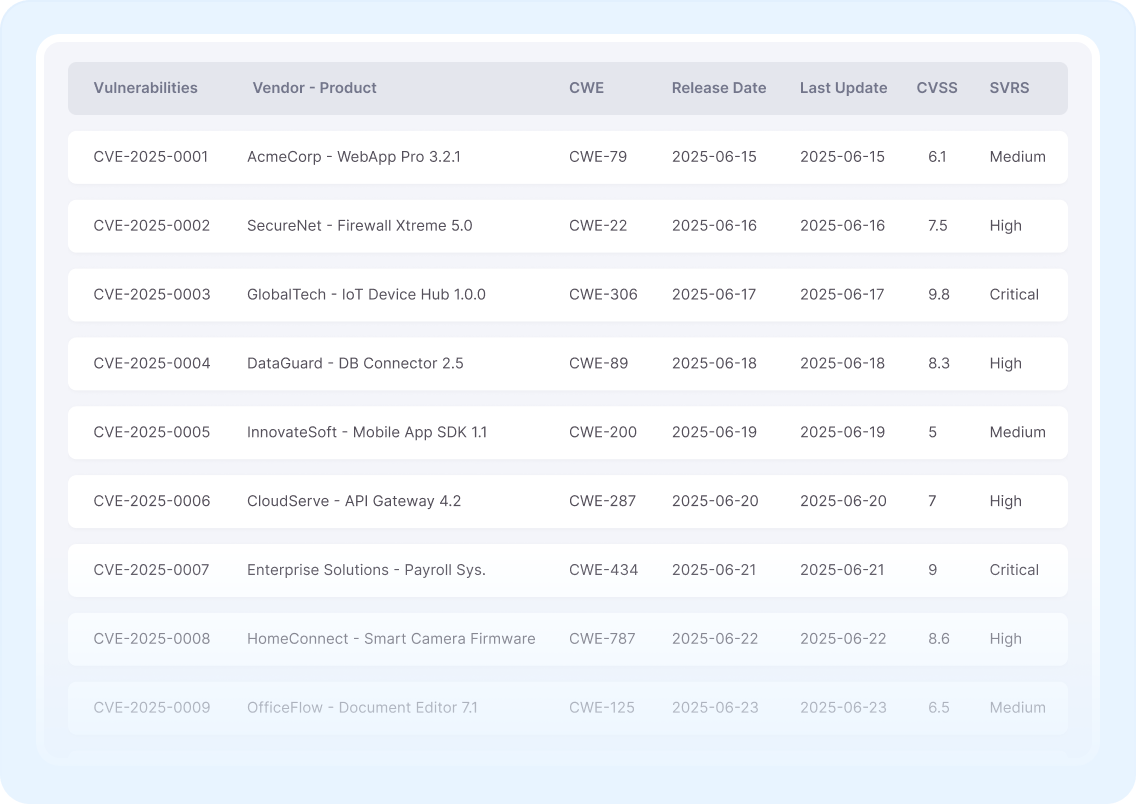
CVE intelligence (contextualized)
Understand vulnerabilities in context with enrichment from exploit data, threat actors, and active campaigns.
Stack-aware vulnerability analysis
Map vulnerabilities to the specific products, vendors, and versions in your assets to assess true exposure and impact depth.
Misconfiguration detection
Identify risky misconfigurations across services and environments before attackers exploit them.
Risk scoring by asset sensitivity
Prioritize issues based on the criticality and business value of affected assets.
Prioritization based on threat actor targeting
Align your defense with intelligence on threat actors actively targeting your industry, tech stack, or geography.
Integration with ticketing/SIEM tools
Automate vulnerability remediation by syncing results directly into your security and operational workflows.
Cypho Secures Your Assets in a World Full of Vulnerabilities
Cypho delivers context-aware vulnerability intelligence with real-time threat correlation and risk-based prioritization across your entire attack surface.
Focus on what’s actively exploited
Stop wasting time on theoretical risks. Cypho highlights vulnerabilities tied to real-world attacker behavior—so your team focuses on threats that truly matter.
Security decisions grounded in business context
Early warning for smarter defense