BRAND IMPERSONATION PREVENTION
Monitor and eliminate fraudulent domains, fake social profiles, and phishing campaigns targeting your growing customer base.
Advanced cybersecurity solutions tailored for growing organizations. As your operations expand, protect increasing digital assets, manage complex infrastructure, and maintain customer trust with enterprise-grade security that scales with your growth trajectory.

Growing businesses face evolving cyber threats as they expand their digital footprint, increase customer base, and attract more sophisticated attackers.
As businesses grow, so does their digital infrastructure including multiple cloud environments, third-party integrations, remote workforces, and customer-facing platforms. Each new system, application, or connection point creates potential vulnerabilities that attackers can exploit. Without comprehensive visibility and continuous monitoring, these expanding attack surfaces become blind spots where threats can emerge undetected. Growing businesses must proactively map, monitor, and secure every entry point to prevent breaches that could derail momentum and damage hard-earned reputation.
Growth often means partnering with vendors and service providers, each introducing potential security weaknesses. A single compromised third-party connection can provide attackers with backdoor access to your systems and customer data. Growing organizations must maintain continuous monitoring of third-party connections to protect against cascading breaches.
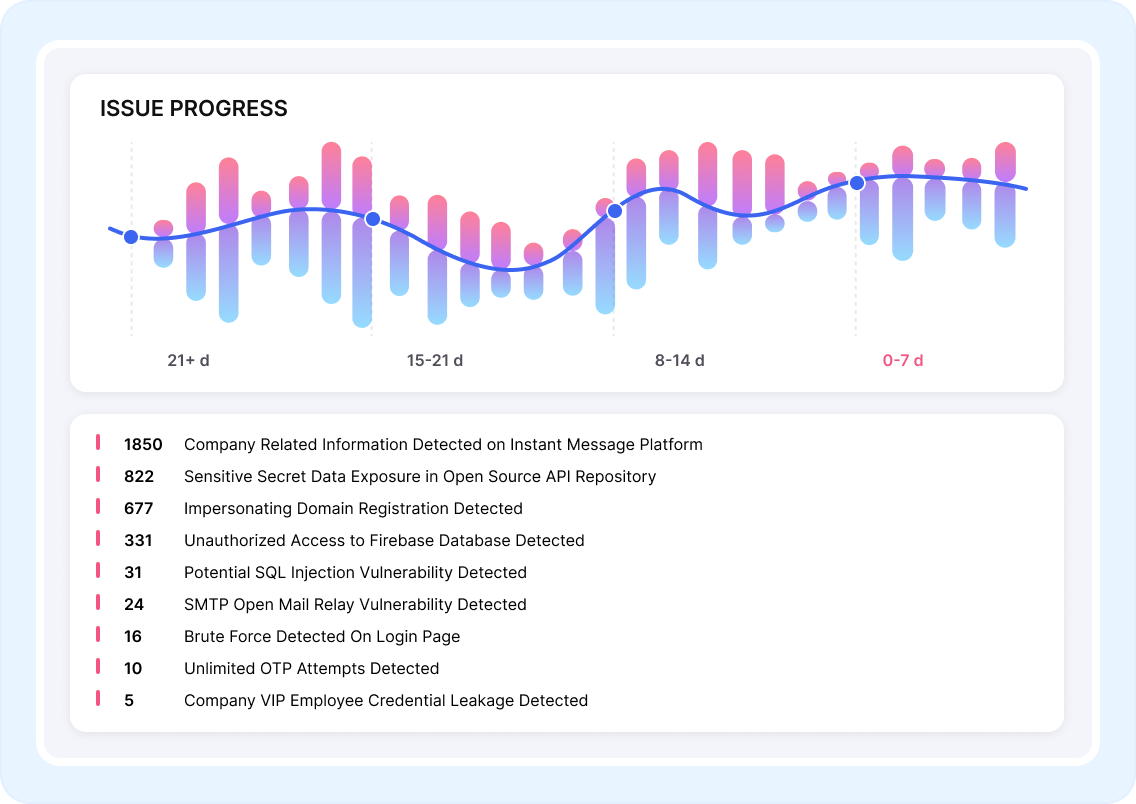
As your brand gains recognition, attackers increasingly target your customers and employees with sophisticated phishing campaigns. Domain spoofing, CEO fraud, and impersonation attacks exploit trust in your growing brand to steal credentials or distribute malware. Without proactive brand protection, these attacks can compromise systems and erode customer confidence.
With expanding teams and increasing access privileges, credential management becomes critical. Stolen or leaked credentials provide attackers with legitimate-looking access to sensitive resources. Growing businesses need robust identity management and continuous dark web monitoring to detect compromised credentials before attackers exploit them.
Growth brings heightened regulatory requirements across GDPR, CCPA, SOC 2, ISO 27001, and industry-specific frameworks. These standards require demonstrable security controls including threat monitoring and vulnerability management. Cypho's platform aligns with key framework controls, providing the visibility and monitoring capabilities needed to support compliance efforts and build customer trust.
Leverage comprehensive cybersecurity capabilities designed to support your expansion while protecting what matters most.
Monitor and eliminate fraudulent domains, fake social profiles, and phishing campaigns targeting your growing customer base.
Detect exposed credentials, proprietary data, and customer information across the dark web and act before breaches escalate.
Gain complete visibility across expanding infrastructure, cloud environments, and digital assets with continuous vulnerability assessment.
Identify and neutralize threats targeting your organization with AI-powered intelligence and automated response capabilities.
Strong security practices protect customer data and demonstrate commitment to privacy, increasing retention and lifetime value.
Robust security posture opens doors to enterprise clients, strategic partnerships, and new markets requiring proven compliance.
Proactive threat detection and incident response capabilities ensure business continuity and minimize disruption during rapid scaling.
Comprehensive security that adapts to your evolving needs without slowing momentum.
Growing businesses need security solutions that scale seamlessly with expanding operations. Cypho provides centralized dashboards offering complete visibility across all digital assets, cloud environments, and third-party connections. Monitor threats, manage vulnerabilities, and coordinate responses from a single unified platform that grows with your organization.
Schedule a demo now