Shifting your security posture from reactive to proactive
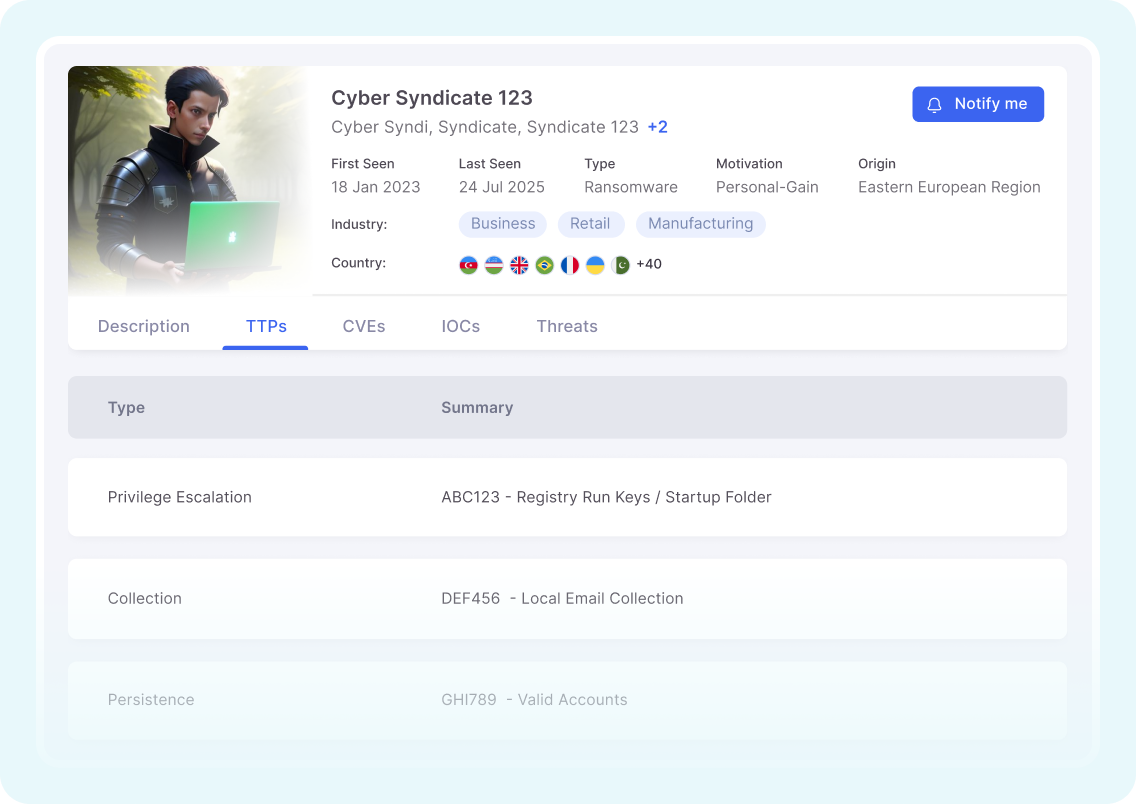
Gain direct visibility into adversary operations by systematically analyzing threat actor TTPs, correlating campaign, and tracking adversary infrastructure. This allows your security team to anticipate emerging threats, enabling the strategic implementation of defensive measures to counterattack methodologies effectively.
Adversary Lifecycle Insights
Empower your organization to analyze, anticipate, and strategically respond to the most sophisticated cyber threats
Threat actor profiling (TTPs, motivations)
Understand adversary profiles by analyzing their Tactics, Techniques, and Procedures (TTPs), along with their underlying objectives.
Campaign monitoring by region/sector
Track and analyze active cyber campaigns, identifying their targeted regions, specific industries, and operational patterns.
MITRE ATT&CK mapping
Correlate observed threat behaviors with the industry-standard MITRE ATT&CK framework for standardized understanding and defensive alignment.
Attribution & adversary infrastructure tracking
Identify the origin of threats and map the networks, tools, and assets used by adversaries in their operations.
Early warning intelligence
Receive timely, actionable intelligence on emerging threats and impending campaigns to enable proactive defensive measures.
Strategic reporting for executives
Deliver high-level, distilled insights on the threat landscape and adversary trends, tailored for executive decision-making and risk management.
Realizing Intelligence Value
Understand the key advantages gained by integrating deep adversary profiling and campaign intelligence into your cybersecurity framework.
Proactive Risk Mitigation
Gain the foresight to anticipate and prevent attacks. By understanding adversary TTPs and evolving campaigns, you can pre-emptively harden critical assets and significantly reduce your attack surface.
Optimized Resource Allocation
Enhanced Strategic Decision-Making
Experience our Threat Actor Tracking firsthand
Discover how to integrate proactive threat tracking into your strategic defense.