Uncovering Hidden Risks For E-commerce business
As online retail scales globally, attackers exploit every digital touchpoint, targeting customers, transactions, and backend systems. Cypho delivers real-time threat intelligence tailored for e-commerce platforms, helping detect and prevent fraud, secure APIs, monitor dark web, and stops attacks before they impact business operations.
Mitigating Real-World Threats for E-commerce Businesses
Surfacing rising threats for e-commerce through continuous monitoring and real-time intelligence.
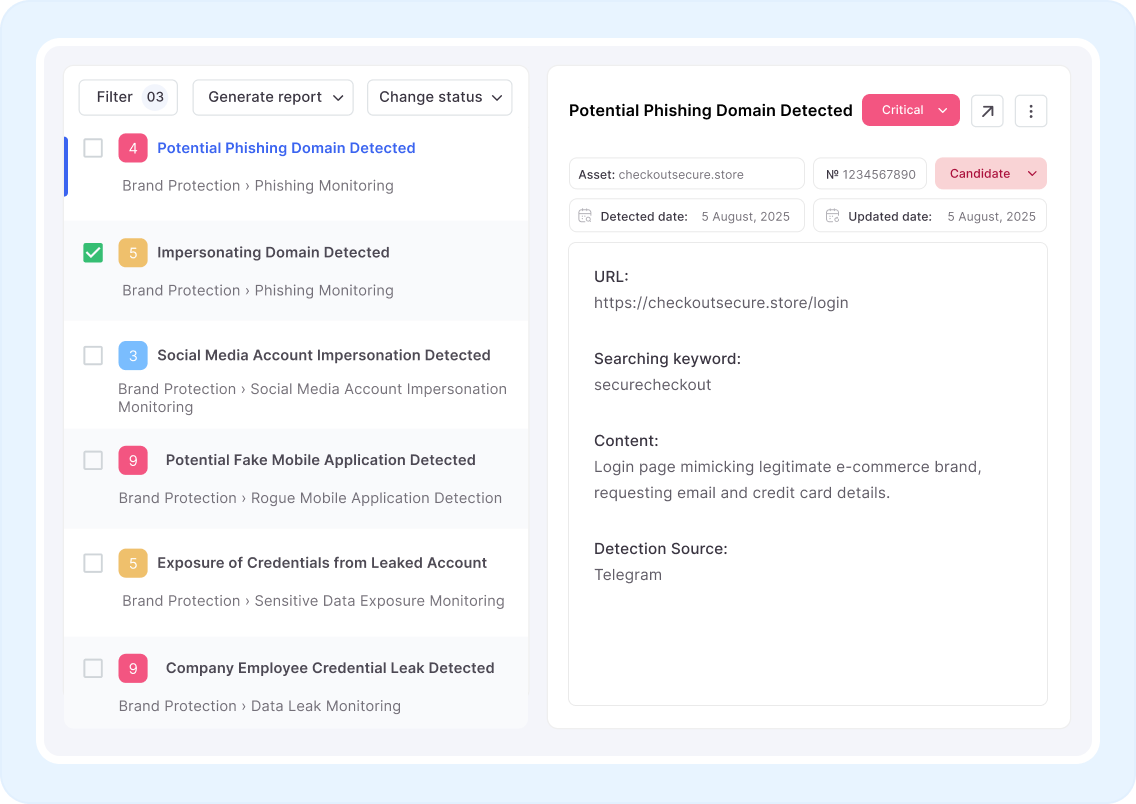
E-skimming & Payment Card Theft
Cybercriminals compromise checkout pages to silently steal customers’ payment card details during online transactions. These attacks are often difficult to detect and can persist until financial institutions or customers report suspicious activity. Cypho continuously monitors domains and connected assets for unusual changes, third-party abuse, and indicators of skimming behavior. By correlating findings with brand abuse campaigns and card leak patterns seen across dark web channels, Cypho delivers context-aware issues that help your security team prioritize investigation and minimize dwell time before customer impact escalates.
API Abuse & Business Logic Attacks
E-commerce platforms depend on APIs for operations. Attackers exploit weak authentication or flawed logic to manipulate carts, prices, or user data. API monitoring helps detect anomalies in request patterns, abuse attempts, and unexpected usage spikes.
Fake Order Bots & DoS Attacks
Malicious bots target e-commerce platforms to flood inventory, place fake orders, or exhaust server resources. Combined with DDoS campaigns, these attacks can crush storefront performance. Identifying non-human traffic patterns helps maintain stability and customer access.
Account Takeovers (ATO)
Credential stuffing and phishing attacks often lead to user account compromises, giving attackers access to saved cards, order histories, or reward systems. Detecting login anomalies and failed attempts is critical for early warning.
Brand Impersonation & Rogue Apps
Attackers create fake websites, social media accounts, and mobile apps to impersonate trusted e-commerce brands. Cypho continuously monitors across web and app platforms, delivering context-rich alerts helping you respond to impersonation threats quickly.
Digital risk monitoring developed with e-commerce in mind
Uncovering the threats e-commerce platforms face every day.
Early detection of data leaks and impersonation
Uncover stolen credit cards, leaked credentials, and actor chatter related to your online store, users, or employees. Cypho delivers actionable intelligence to support fraud prevention and incident response.
Digital brand protection across web and mobile
Maintain oversight in cyber threat intelligence