Securing Government Institutions from Evolving Cyber Threats
Government institutions face some of the highest levels of cyber risk—from nation-state actors to ransomware gangs. Cypho equips public-sector organizations with real-time threat intelligence, helping protect sensitive data, safeguard critical infrastructure, and prevent cyber attacks before they escalate.
Protecting Public Sector from Advanced Threats
With expanding digital services and sensitive citizen data, even a single vulnerability can open the door to national-scale consequences.
Protection of Sensitive Citizen Data
Governments manage large volumes of confidential data — ranging from citizen identity records, tax and healthcare information, and social service data to election systems, immigration records, and public safety databases. Much of this data is shared across agencies, increasing the risk of exposure that can lead to identity theft, erode public trust, and disrupt essential services.Safeguarding citizen data is essential to maintaining the reliability of government services and minimizing the reputational, operational, and strategic impact of potential breaches.
Ransomware & State-Sponsored Threats
Ransomware and state-sponsored attacks can disrupt critical government services and target strategic assets like defense systems, policy data, and diplomatic communications — posing both operational and security risks.
Cloud Security & Exposure of Public-Facing Assets
Misconfigured storage buckets, exposed APIs, and forgotten subdomains increase the attack surface, making it easier for adversaries to find and exploit vulnerabilities.
Email Spoofing & Phishing Attacks
Adversaries frequently spoof government domains to send malicious emails to both citizens and internal staff. These campaigns can result with malware infections, disinformation, or unauthorized access to internal systems.
Legacy Systems with Vulnerabilities
Outdated software makes it difficult to patch or integrate with modern security tools, creating blind spots across critical infrastructure.
Intelligence solutions for government cybersecurity
Targeted solutions that strengthen defense, improve visibility, and support informed decision-making across departments and organizations.
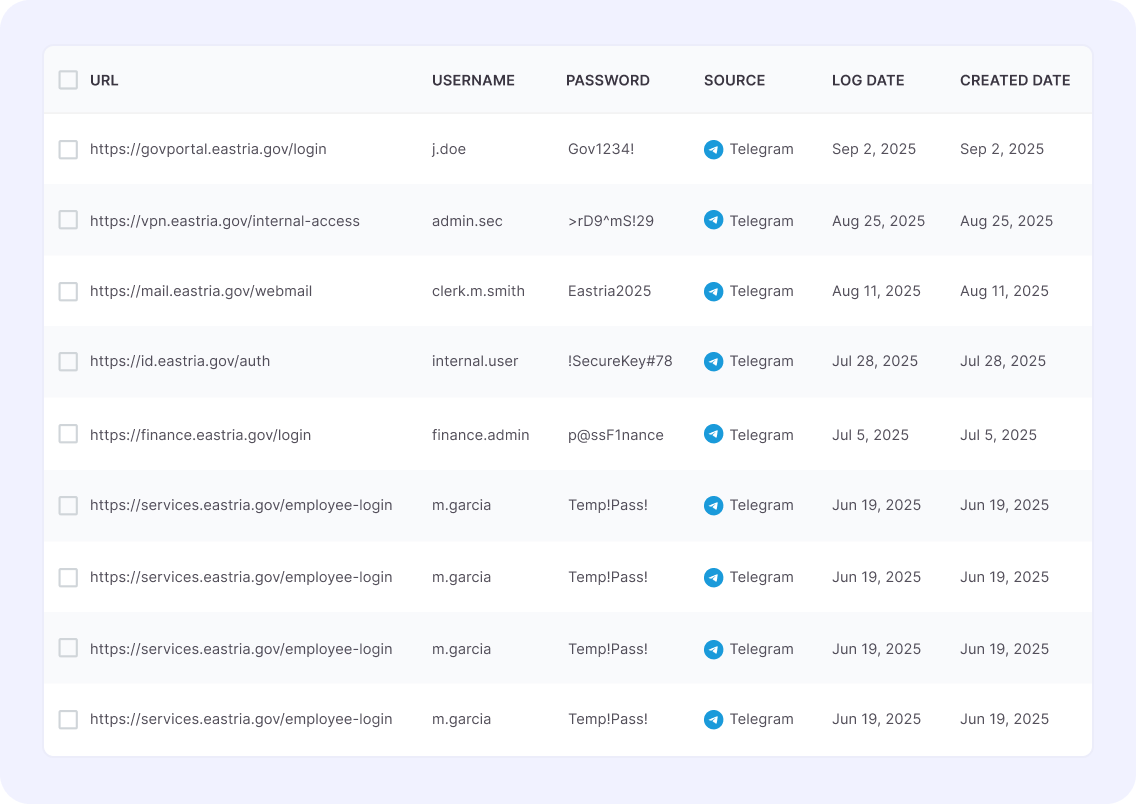
Early detection of data leaks and impersonation
The risk of digital impersonation and data exposure on the dark web is high. Cypho’s dark web and brand monitoring modules alert agencies to leaked credentials, exposed documents, and impersonation attempts to mitigate risks.
Secure exposure management for public-facing assets
Strategic intelligence for national cyber defense