Actionable Cyber Threat Intelligence
Digital transformation and a rapidly growing threat landscape make it harder to detect and resolve cyber risks. Cypho tackles this by continuously monitoring millions of threat signals and linking them to your organization’s assets. We correlate raw intelligence and your digital footprint — giving you real-time visibility into risks from open, deep, and dark web sources. Get the latest alerts, understand what’s targeting you, and take control before threats turn into impact.
Get a Demo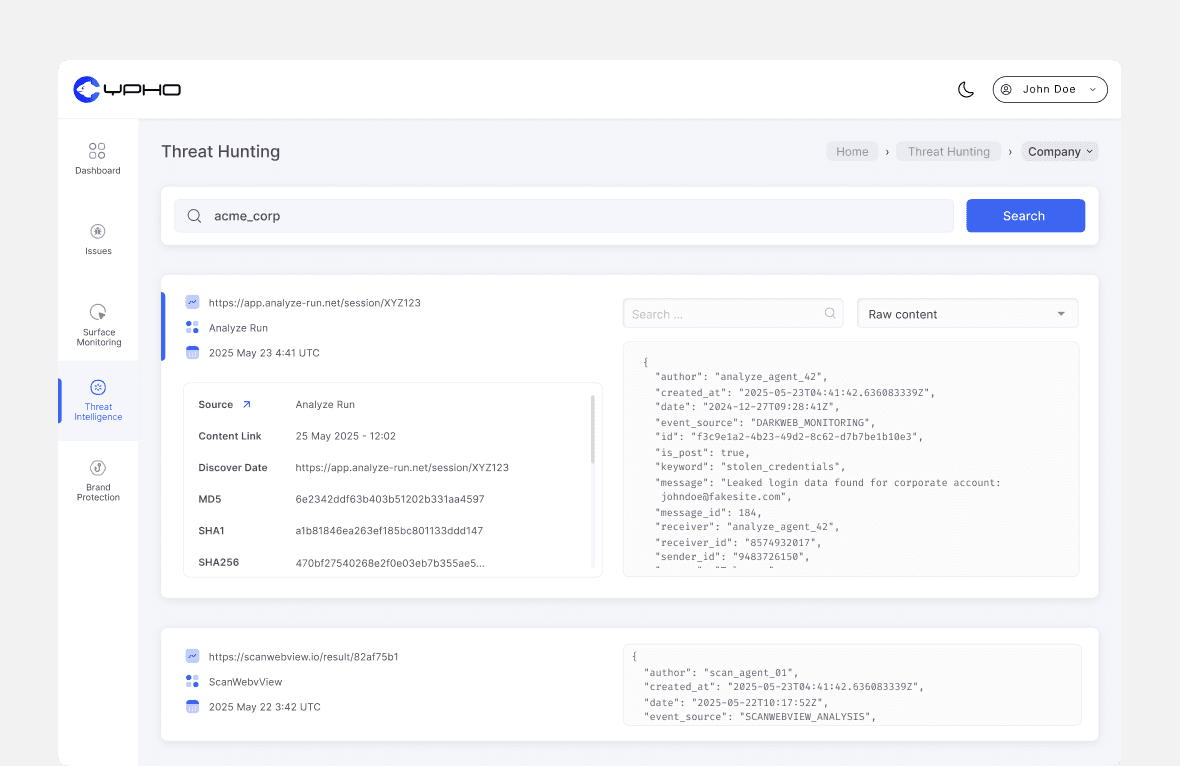
Use cases
Securing your mission-critical infrastructure
Cyber Threat Intelligence Scope
Holistic coverage of digital business risk areas
Advanced Threat Hunting
Our threat hunting solution helps you move from passive defense to active detection. It uncovers both known and unknown threats, using predictive techniques to turn raw signals into actionable intelligence.
By staying ahead of emerging risks, predictive threat hunting gives your team the insight detects early, respond faster, and reduce impact — before threats cause damage.

Threat Landscape
Cypho’s Threat Landscape connects threat data into a unified dashboard built for strategic insight. It helps you spot patterns in attacker activity, identify impacted regions and industries, - you can stay one step ahead of the risks that matter most to you.
The landscape combines intelligence from dark web and surface web sources, highlights notable CVEs, and shows victim trends by sector and geography. It offers a broader perspective without overwhelming detail — making it easier to track emerging threats, understand who’s being targeted, and align your security priorities accordingly.

Threat Actor Intelligence
Cypho helps you monitor and analyze the groups behind cyberattacks — from nation-state APTs and financially motivated ransomware gangs to hacktivists, cybercriminals, and insider threats. We reveal who’s behind the activity — and what they’re targeting. Our threat actor intelligence brings together:
- Real-time visibility into active threat groups and their campaigns
- Threat actor profiles enriched with known tactics, techniques, and linked CVEs
- Victim trends across countries and sectors
- Categorization by actor type, origin, and intent
You can explore and subscribe to actor profiles to focus on what matters most to your organization — whether you're tracking known groups, following recent incidents, or building your defense strategy around how these actors operate.

Vulnerability Intelligence
Cypho’s vulnerability intelligence is your live feed of known exploits — enriched with known vulnerabilities (CVEs) with key scores like CVSS and SVRS. It continuously collects and organizes CVEs across a wide range of technologies. You can easily filter and search through this data.
When a vulnerability is found in a technology or service you use — whether auto-detected or manually added — we deliver instant alerts with detailed context helping you assess, prioritize, and fix the exposure risk before it becomes a problem.

CVE Landscape
The CVE Landscape gives you a focused view of on-trend common vulnerabilities and exploits discovered in the last 30 days. With X platform feed integration, you can view posts from security experts and thought leaders, offering real-time insights into how the community is reacting to newly disclosed CVEs.

Enriched Threat Feed & IoC Management
Actionable threat data and IoCs in one place — organized, customizable, and ready to deploy.
Daily Threat Insights
Cypho provides dynamic dashboards showing daily threat trends, categorized by type and severity to help teams stay ahead of threats.
Custom Repositories
Create tailored feeds based on threat type, update rate, or source to track specific malware, actor groups, or any targeted threat stream.
Flexible Export Options
Export threat data in various formats (JSON, TAXII, CSV.) for easy integration and sharing across tools and teams.

Layers of Cyber Threat Intelligence
Our cyber intelligence framework spans from raw technical data to high-level strategic insights — tailored for analysts, defenders, and executives.
Tactical Intelligence
Tactical intelligence uncovers real-time behavior, tool, and techniques of threat actors. SOC teams use it to fine-tune detection rules, develop response playbooks, and red team simulations. This intelligence is often mapped to frameworks like MITRE ATT&CK, making it easier to build defenses around real-world adversary behavior.
Cyber Threat Intelligence Coverage & Data Sources
Cypho combines intelligence from key source types to give you the most relevant, timely, and contextual threat visibility.
Open Source Intelligence (OSINT)
Open Source Intelligence (OSINT)
Publicly available threat data collected from trusted repositories, security research blogs, paste sites, and community-driven feeds. OSINT helps uncover known indicators, leaked data, and early signs of malicious activity — giving teams a broader view of emerging threats across the internet.
Commercial Threat Feeds
Commercial Threat Feeds
Curated intelligence from premium sources, covering malware trends, ransomware groups, phishing campaigns, and emerging attack vectors.
Human Intelligence (HUMINT)
Human Intelligence (HUMINT)
Cypho monitors human-driven channels - encrypted chats, or invite-only marketplaces, to uncover early warnings about planned attacks, breach claims, or shared exploits. This gives your team visibility into threats before they surface elsewhere.
Technical Intelligence
Technical Intelligence
Raw threat signals including IPs, file hashes, domains, SSL certs, and malware behavior — collected from global threat monitoring systems.
Customer-sourced intelligence
Customer-sourced intelligence
Signals from your environment, including integrated assets, internal incidents, and customer-specific configurations, provide the context needed to detect and prioritize real threats.
Dark Web
Dark Web
Actionable insights from hidden forums, marketplaces, and leak sites — uncovering compromised data, threat actor chatter, breached credentials, and emerging cybercrime trends.
Curated intelligence from premium sources, covering malware trends, ransomware groups, phishing campaigns, and emerging attack vectors.
Cypho monitors human-driven channels - encrypted chats, or invite-only marketplaces, to uncover early warnings about planned attacks, breach claims, or shared exploits. This gives your team visibility into threats before they surface elsewhere.
Raw threat signals including IPs, file hashes, domains, SSL certs, and malware behavior — collected from global threat monitoring systems.
Signals from your environment, including integrated assets, internal incidents, and customer-specific configurations, provide the context needed to detect and prioritize real threats.
Actionable insights from hidden forums, marketplaces, and leak sites — uncovering compromised data, threat actor chatter, breached credentials, and emerging cybercrime trends.
Uncover and outpace cyber threats
Real-time threat intelligence tailored to your digital environment




